Top Cyber Attacks in 2025: Major Breaches and Critical Lessons Learned
Introduction: The Escalating Cyber Battlefield of 2025
Imagine waking up to find your bank account emptied, your personal data exposed, or your entire company held hostage by digital attackers. This isn't science fiction—it's the reality of 2025's cybersecurity landscape. As our world becomes increasingly digital, the stakes have never been higher.
According to the 2025 Cyber Threat Report, cyber attacks have increased by 67% compared to 2024, with damages projected to exceed $12 trillion globally. The combination of sophisticated AI-powered attacks, vulnerable IoT devices, and geopolitical tensions has created a perfect storm for digital security.
In this comprehensive analysis, we'll examine the most significant cyber attacks of 2025, understand how they happened, and most importantly—extract crucial lessons to protect yourself and your organization.
The Changing Face of Cyber Threats in 2025
Cyber attacks have evolved dramatically. While ransomware and phishing remain common, 2025 has seen the rise of several new threat vectors:
- AI-powered social engineering: Attackers use generative AI to create highly personalized phishing campaigns
- Supply chain attacks: Compromising software vendors to infect thousands of organizations simultaneously
- Quantum computing threats: Early-stage attacks targeting current encryption methods
- Deepfake blackmail: Using AI-generated content for extortion schemes
The FBI's Internet Crime Report indicates that reported losses have tripled since 2023, with businesses and individuals equally vulnerable.
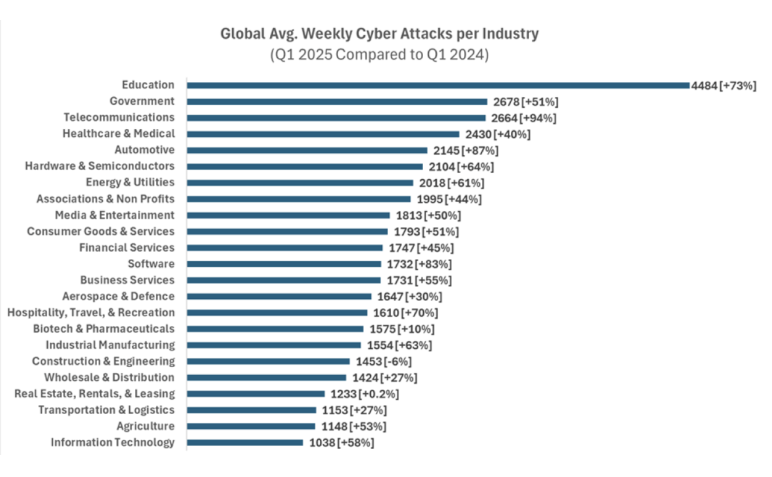
Suggested alt text: Infographic showing rising cyber attack trends and types in 2025
Major Cyber Attacks of 2025: Case Studies
1. The Global Healthcare Ransomware Attack (January 2025)
In what security experts are calling "the digital pandemic of 2025," a coordinated ransomware attack targeted hospital systems across North America and Europe simultaneously.
How it happened: Attackers exploited vulnerabilities in legacy medical devices connected to hospital networks. The ransomware, dubbed "MedLock," encrypted patient records, appointment systems, and even critical care equipment.
Impact: Over 300 hospitals affected, emergency services disrupted, and an estimated $2.3 billion in damages including ransom payments and recovery costs.
Lesson learned: Critical infrastructure must segment networks, regularly update legacy systems, and maintain air-gapped backups. The healthcare sector's vulnerability highlighted the life-or-death stakes of cybersecurity.
2. Cloud Service Provider Supply Chain Attack (March 2025)
A major cloud services company suffered a sophisticated supply chain attack that compromised thousands of their clients, including Fortune 500 companies and government agencies.
How it happened: Attackers infiltrated the company's software development pipeline and inserted malicious code into a routine security update. When customers installed the update, it created backdoors in their systems.
Impact: Data breach affecting 87 million users, intellectual property theft from multiple corporations, and temporary shutdown of critical business operations.
Lesson learned: Organizations must implement software supply chain security measures, verify updates through multiple channels, and adopt zero-trust architectures. No vendor can be fully trusted without verification.
3. AI-Powered Phishing Campaign (May 2025)
This attack demonstrated how generative AI has lowered the barrier to entry for sophisticated social engineering attacks.
How it happened: Using AI voice and video generation tools, attackers created convincing deepfake messages from company executives authorizing fund transfers. The AI could mimic speech patterns and mannerisms with frightening accuracy.
Impact: Over $450 million stolen from corporations worldwide before the scheme was uncovered. Several CFOs and financial controllers lost their jobs despite being victims of sophisticated technology.
Lesson learned: Multi-factor authentication and verification protocols must include out-of-band confirmation for financial transactions. Employee training must evolve to recognize AI-generated manipulation attempts.

Suggested alt text: Side-by-side comparison of traditional phishing email vs AI-generated phishing attempt
4. Critical Infrastructure DDoS Attack (July 2025)
A distributed denial-of-service attack targeted power grid control systems across multiple states, causing temporary blackouts and service disruptions.
How it happened: Attackers exploited vulnerable IoT devices in consumer homes (smart thermostats, security cameras) to create a massive botnet that overwhelmed utility company networks.
Impact: Power outages affecting approximately 1.2 million customers for several hours, economic impact estimated at $900 million, and heightened concerns about national security vulnerabilities.
Lesson learned: Critical infrastructure protection must extend to consumer IoT devices that can be weaponized. Regulation and security standards for IoT manufacturers need strengthening.
5. Cryptocurrency Exchange Collapse (September 2025)
One of the world's largest cryptocurrency exchanges was hacked through a novel combination of technical and social engineering attacks.
How it happened: Attackers first compromised several employees through personalized phishing campaigns, then used their credentials to bypass multi-factor authentication through SIM-swapping attacks. Once inside, they manipulated smart contracts to drain wallets.
Impact: $1.8 billion in cryptocurrency stolen, exchange bankruptcy, and massive losses for investors. The incident triggered increased regulatory scrutiny of crypto exchanges worldwide.
Lesson learned: Cryptocurrency exchanges need stronger security protocols beyond standard multi-factor authentication. Hardware security keys, behavioral analytics, and separation of duties are essential for financial platforms.
Emerging Threat Vectors in 2025
Beyond these major incidents, security researchers have identified several emerging threats:
AI-Powered Vulnerability Discovery
Attackers are using AI systems to automatically discover and exploit vulnerabilities faster than humans can patch them. According to TechCrunch, AI-generated exploits have reduced the average "patch gap" from 45 days to just 7 days.
Quantum Computing Threats
While practical quantum computers remain years away, threat actors are already harvesting encrypted data today that they can decrypt once quantum computers become available—a strategy called "harvest now, decrypt later."
5G Network Vulnerabilities
The rapid rollout of 5G networks has created new attack surfaces, particularly in network slicing and edge computing implementations. Security often lags behind deployment.
Suggested alt text: Diagram showing relationships between emerging cyber threats including AI, quantum, and 5G vulnerabilities
Key Cybersecurity Lessons from 2025 Attacks
These incidents provide valuable insights for individuals and organizations:
1. Assume Breach Mentality
Instead of focusing solely on prevention, organizations must assume they will be breached and design systems accordingly. This includes implementing robust detection, response, and recovery capabilities.
2. Zero Trust is Non-Negotiable
The principle of "never trust, always verify" must be applied throughout digital environments. This includes network segmentation, least privilege access, and continuous verification.
3. Supply Chain Security is Critical
Organizations must vet their vendors' security practices and implement measures to detect compromises in third-party software and services.
4. Employee Training Must Evolve
Traditional security awareness training is insufficient against AI-powered social engineering. Training must include realistic simulations and focus on verification protocols.
5. Backup and Recovery Plans Save Organizations
Companies with robust, tested backup and recovery procedures suffered significantly less damage from ransomware attacks. The 3-2-1 backup rule (three copies, two media types, one offsite) proved invaluable.
Protective Measures for 2025 and Beyond
Based on these lessons, here are essential protective measures:
For Individuals:
- Use hardware security keys for important accounts
- Enable multi-factor authentication everywhere possible
- Regularly review privacy settings and connected applications
- Use a password manager with unique passwords for each service
- Be skeptical of unsolicited communications, even if they appear to come from known contacts
For Organizations:
- Implement zero-trust architecture
- Conduct regular security awareness training with phishing simulations
- Establish and test incident response plans
- Segment networks to limit lateral movement
- Monitor supply chain security and conduct regular audits
- Invest in threat intelligence and security monitoring services
The Future of Cybersecurity: 2026 Predictions
Looking ahead, cybersecurity experts predict:
- Increased regulation following major incidents, particularly for critical infrastructure
- AI-based defense systems becoming more common to counter AI-powered attacks
- Greater focus on resilience and recovery capabilities rather than just prevention
- Workforce shortages driving automation in security operations
- Quantum-resistant cryptography becoming standard for new systems
Conclusion: Vigilance in the Digital Age
The cyber attacks of 2025 demonstrate that digital security is everyone's responsibility. From individuals protecting their personal data to organizations safeguarding critical infrastructure, vigilance and proactive measures are essential.
While threats continue to evolve, so do our defenses. By learning from these incidents, implementing best practices, and maintaining a security-first mindset, we can navigate the digital landscape more safely.
What's your biggest cybersecurity concern? Share your thoughts in the comments below, and subscribe for more security insights!
(1).png)