How to Recognize and Avoid Phishing Emails: 2025 Step-by-Step Guide
(toc) #title=(Table of Content)Introduction: The Phishing Epidemic of 2025
You check your email and see a message from your bank: "Urgent: Your account has been compromised. Click here to secure it immediately." Your heart races—should you click? In 2025, this scenario plays out millions of times daily, and increasingly, people are falling for it.
Phishing attacks have evolved from clumsy Nigerian prince scams to sophisticated operations that mimic legitimate communications perfectly. According to the FBI's Internet Crime Complaint Center, phishing was the #1 cyber crime in 2024, costing victims over $4.6 billion—and 2025 is on track to be even worse.
The scary part? Modern phishing emails often bypass spam filters and look identical to real messages from companies you trust. But here's the good news: with the right knowledge, you can spot these fraudulent attempts every time. This comprehensive guide will show you exactly how.
What Exactly is Phishing? Beyond the Basic Definition
Phishing is a cyber attack where criminals impersonate legitimate organizations to steal sensitive information: passwords, credit card numbers, social security numbers, or access to your accounts. The term "phishing" combines "fishing" — as in fishing for information — with "ph" from early hacker culture.
In 2025, phishing has evolved into several specialized forms:
- Spear phishing: Targeted attacks against specific individuals using personal information
- Whaling: Attacks targeting high-level executives or important figures
- Smishing: Phishing via SMS/text messages
- Vishing: Phishing via voice calls (phone scams)
- AI-powered phishing: Using generative AI to create perfectly written messages
The Anti-Phishing Working Group reports that unique phishing websites detected in Q1 2025 increased by 58% compared to 2024, showing this threat is growing rapidly.
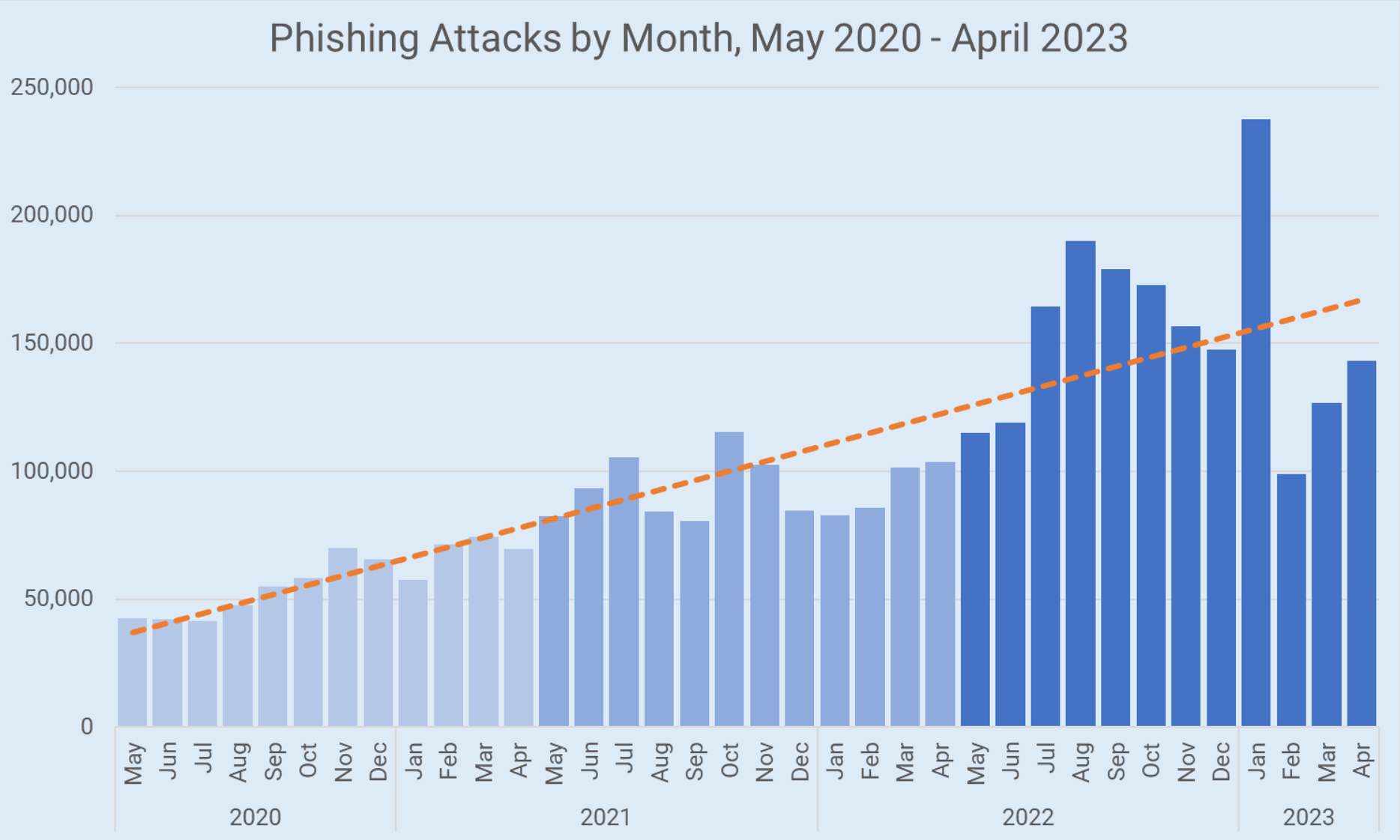
Suggested alt text: Timeline showing sophistication increase in phishing attacks from crude emails to AI-generated messages
10 Red Flags: How to Spot Phishing Emails Immediately
While phishing emails are becoming more sophisticated, they still contain telltale signs. Here are the most common red flags to watch for:
1. Urgent or Threatening Language
Phishers create false urgency to bypass your critical thinking. Look for phrases like:
- "Immediate action required"
- "Your account will be suspended"
- "Final warning"
- "24 hours to respond"
Legitimate companies rarely use such pressure tactics in initial communications.
2. Generic Greetings
Phishing emails often use generic openings like "Dear Customer" or "Dear User" instead of your actual name. While some legitimate bulk emails might do this, combined with other red flags, it's suspicious.
3. Suspicious Sender Addresses
Always check the actual email address, not just the display name. Phishers often use addresses that resemble legitimate ones but have slight alterations:
- support@amazon-security.com (instead of @amazon.com)
- service@paypal-users.net (instead of @paypal.com)
- account@apple-support.xyz (instead of @apple.com)
4. Poor Grammar and Spelling
While AI has improved phishing grammar, many still contain errors. Professional companies have editors review their customer communications—multiple mistakes are a strong indicator of phishing.
5. Requests for Sensitive Information
Legitimate companies will never ask for passwords, social security numbers, or credit card information via email. Any email requesting this information is almost certainly fraudulent.
6. Mismatched URLs
Hover over links (without clicking!) to see the actual URL. Phishers often use legitimate-looking text that hides malicious links.
7. Unexpected Attachments
Unexpected email attachments, especially from unknown senders, are a major red flag. These can contain malware that installs when opened.
8. Too Good to Be True Offers
"You've won a free iPhone!" or "Claim your $1000 gift card now!"—if it seems too good to be true, it almost always is.
9. Inconsistent Branding
Look for slight logo alterations, wrong colors, or low-quality images. Professional companies maintain consistent branding.
10. Strange From Fields
Check that the "From" field matches the company domain. Also watch for reply-to addresses that differ from the sender address.
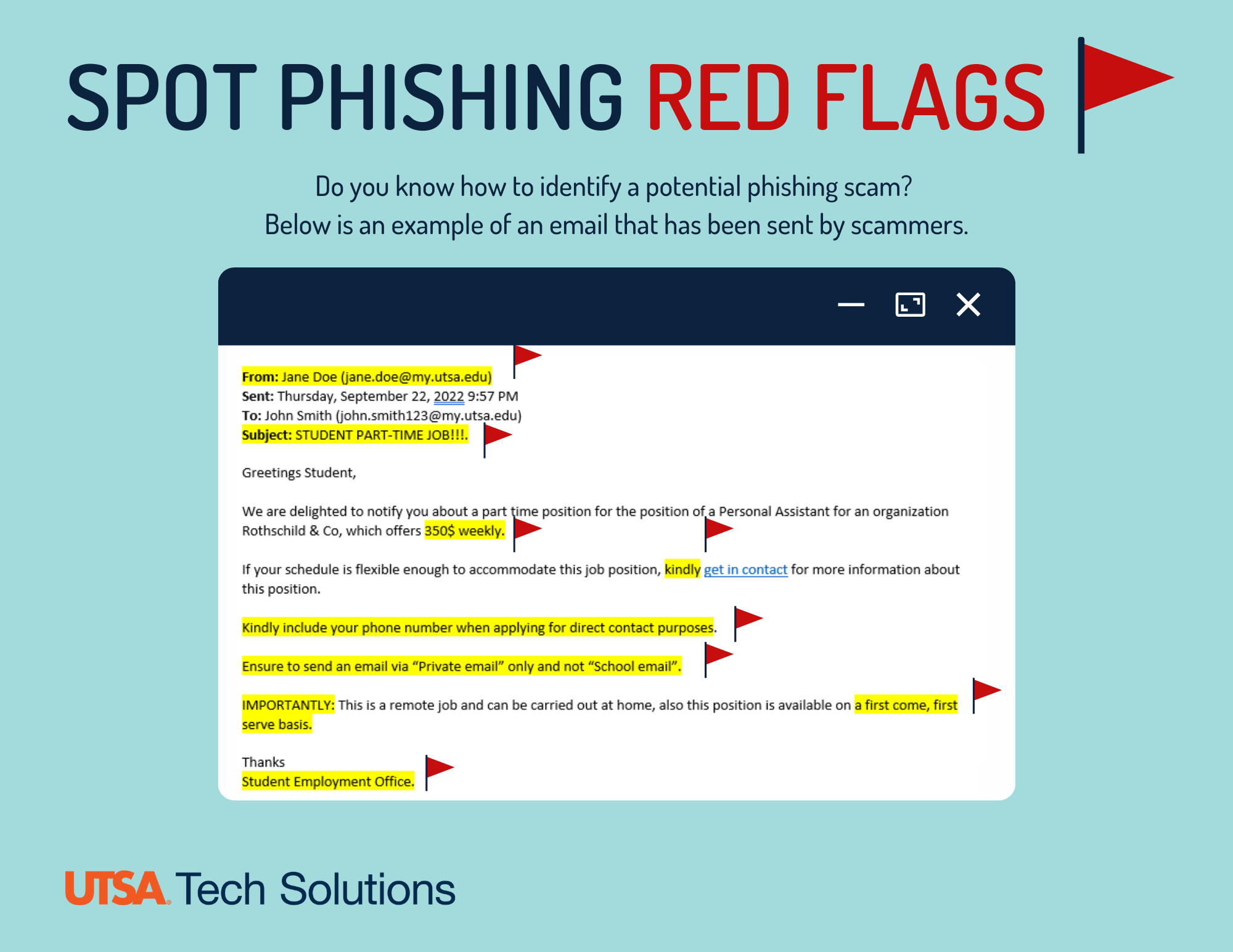
Suggested alt text: Annotated phishing email showing 10 common red flags with callouts
Step-by-Step: How to Analyze a Suspicious Email
When you receive a potentially suspicious email, follow this step-by-step process:
Step 1: Don't Panic or Click Anything
Phishers rely on emotional responses. Take a deep breath and don't click any links or download attachments.
Step 2: Examine the Sender Details
Look at the actual email address, not just the display name. Check for slight misspellings or strange domains.
Step 3: Check the Greeting and Content
Is it personalized with your name? Does the content make sense based on your relationship with the company?
Step 4: Hover Over Links
Mouse over any links (without clicking) to see the actual URL in your browser's status bar. Does it match the company's legitimate domain?
Step 5: Look for Contact Information
Legitimate emails usually include official contact details. Phishing emails often lack these or provide fake information.
Step 6: Verify Through Other Channels
If you're unsure, contact the company directly using a phone number or website you know is legitimate—not any contact information provided in the suspicious email.
Step 7: Report and Delete
Report phishing attempts to your email provider and the impersonated company, then delete the email.
Real-World 2025 Phishing Examples (And How to Spot Them)
Let's examine actual phishing templates circulating in 2025:
Example 1: The Bank Security Alert
Subject: URGENT: Suspicious Activity Detected on Your Account [#32987]
Body: "We detected unusual login activity from a new device in Miami, FL. If this wasn't you, please verify your identity immediately by clicking here to prevent account suspension."
How to spot it: Creates false urgency, generic greeting, hover shows link goes to "secure-bank-login.com" instead of actual bank domain.
Example 2: The Package Delivery Scam
Subject: Action Required: Your Package Delivery is On Hold
Body: "UPS attempted delivery but failed due to address issues. Click here to update your delivery information or your package will be returned to sender."
How to spot it: You weren't expecting a package, sender email is "support@ups-delivery.org" (not @ups.com), contains attachment called "Delivery_Label.exe".
Example 3: The Netflix Payment Issue
Subject: Update Your Payment Method to Continue Enjoying Netflix
Body: "We're having trouble processing your payment. Please update your billing information to avoid service interruption."
How to spot it: Greets you as "Dear Netflix User" instead of your name, link goes to "netflix-billing.com" instead of netflix.com, requests credit card information directly in email.
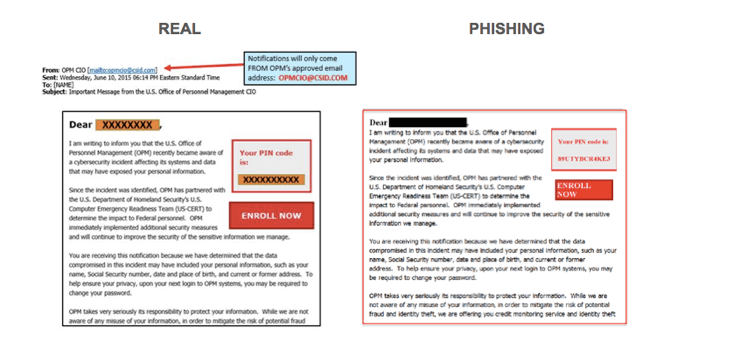
Suggested alt text: Comparison showing legitimate Netflix email vs phishing attempt with annotations
Advanced 2025 Phishing Tactics: AI and Beyond
Phishers are leveraging new technologies to create more convincing attacks:
AI-Generated Content
Generative AI can now create perfectly written emails without grammar errors. Some phishers even use AI to mimic writing styles of specific people.
Deepfake Audio and Video
In spear phishing attacks, criminals might use AI-generated audio or video of executives to authorize fraudulent transactions.
QR Code Phishing
Instead of malicious links, some emails contain QR codes that lead to phishing sites when scanned—bypassing some security filters.
Multi-Channel Attacks
Phishers might send an email followed by a text message or phone call to increase legitimacy.
Protective Measures: Beyond Recognition
Recognizing phishing is crucial, but prevention is even better:
Email Security Settings
- Enable spam filters provided by your email provider
- Use email rules to filter suspicious messages
- Disable automatic image loading in emails
Technical Protections
- Keep your operating system and browsers updated
- Use antivirus software with phishing protection
- Enable multi-factor authentication on all accounts
- Use a password manager to avoid entering credentials on phishing sites
Personal Practices
- Never reuse passwords across different sites
- Regularly check your account statements for suspicious activity
- Educate family members and colleagues about phishing risks
- When in doubt, contact companies through verified channels
What to Do If You've Fallen for a Phishing Attack
If you suspect you've been phished, act immediately:
- Disconnect from the internet to prevent further data transmission
- Change your passwords immediately, starting with email and financial accounts
- Contact your bank if financial information was compromised
- Scan your device for malware using updated security software
- Monitor your accounts for suspicious activity
- Report the phishing attempt to the impersonated organization and relevant authorities
Conclusion: Empowerment Through Awareness
Phishing attacks will continue evolving, but your ability to recognize them can evolve faster. The key is maintaining healthy skepticism—question unexpected emails, verify through trusted channels, and remember that no legitimate organization will pressure you into immediate action or ask for sensitive information via email.
By understanding the red flags, following the step-by-step verification process, and implementing protective measures, you can significantly reduce your risk of falling victim to these attacks. Your awareness is your best defense.
Have you encountered a suspicious email recently? Share your experience in the comments below (without sharing sensitive information), and subscribe for more cybersecurity tips!
(1).png)